Published Aug 30, 2022
By Qredo Team
What Are Threshold Signatures?
Threshold Signatures are a critical part of Qredo's cryptographic toolbox.
In this post, we explain — without math or jargon — how Qredo uses Threshold Signatures to remove the vulnerability of private keys and enable the control of digital assets to be shared across a decentralized network.
What is a digital signature?
In a nutshell, digital signatures are simply cryptographic codes that are used to prove the transaction being sent comes from you.
To achieve this, the signatures are derived from something that only you have: your private key.
Public key cryptography
Public key cryptography provides the basis for securely sending and receiving blockchain transactions. It does this by using a key pair system:
Private keys are secret codes that must not be shared as they grant control over assets.
Public keys can be shared without endangering funds. They are derived from the private key via a one-way cryptographic function, and are used to generate addresses to receive funds, and to verify the authenticity of transactions.
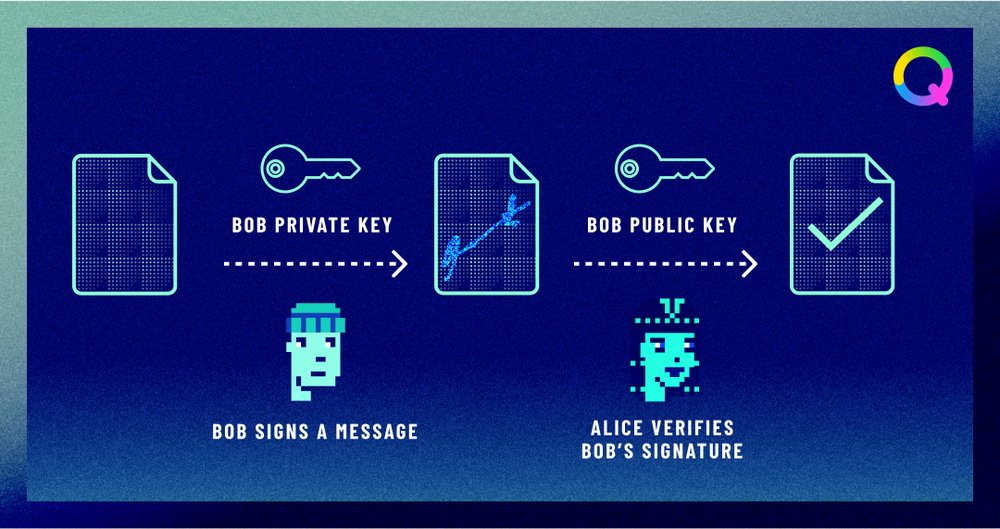
How are digital signatures created?
Digital signatures, such as ECDSA (Elliptic Curve Digital Signature Algorithm) in Bitcoin, are created using the private key and the transaction data.
This process, which relies on complex elliptic curve cryptography, means the signature can only be produced with knowledge of the private key. But, because it is produced using a one-way cryptographic function, the signature doesn't give away any private key information — enabling senders to authenticate transactions without endangering their assets.
Threshold signatures are generated using a similar process. But instead of relying on a single private key, they use multi-party computation (MPC) to produce a signature from private key material distributed between multiple computers.
What are Threshold Signatures?
A threshold signature scheme (TSS) is a method for generating a single digital signature from multiple signers.
The resulting signature looks the same as one created without the threshold scheme, but it is not created with a single private key. Rather, it is created with multiple private key shares, which are distributed such that no single person controls the private key entirely.
To sign a transaction, enough Approvers must participate to meet a threshold. This threshold structure is typically conceptualized as “t of n”, in which n refers to the total number of signers, and t refers to the number of Approvers who can sign a transaction on behalf of the entire group. For example, you might have a group of 7 signers (n), and require 4 of them to authenticate a transaction: t of n = 4 of 7.
How Qredo uses Threshold Signatures
Qredo uses a Threshold Signature Scheme (TSS) implemented with multi-party computation (MPC) to remove the vulnerability of signing with a single private key and create wallets that are controlled by multiple parties.

Each Qredo Wallet has a Custodial Policy. This policy defines a set of Approvers (who must approve the transaction). The policy is defined as a boolean rule.
For example, the following policy requires at least 1 of the Approvers and 2 of the Traders.
Approver1 or Approver2) and (Trader1 + Trader2 + Trader3 >=2
The rules can be organized in subsets and thresholds that map to specific organizational requirements.
When a Trader initiates a transaction, and it is approved by the requisite number of Approvers to meet the threshold, then all of the individual BLS signatures are aggregated into one.
This aggregated signature is pushed onto Qredo Network, where the Validators verify it against the public keys of all the participants. If the aggregated signature has been signed by sufficient participants to satisfy the policy, then Qredo Network invokes the MPC protocol to sign a transaction on the underlying blockchain.
This process has two big advantages over signing transactions with a single private key:
The single point of failure is removed — massively reducing the attack surface and making theft almost impossible.
A large number of approvers, traders and administrators can be assigned different levels of control, enabling digital assets to be managed effectively with even the most complex trade approval flows.
To learn more about Qredo's implementation of Threshold Signatures, download the yellow paper:
